John Doe Strikes Again | n00bzCTF | OSINT
Given is the following:
John Doe has escaped our high secruity prison again!
We managed to intercept an xor key that he uses to send encrypted messages to people!
Your aim is to find classified information on his top secret website!
Start with the encrypted message -
b'\x13\x00\x1d-A*!\x00Q\x16R\x02\x12\x07\n\x1b>\x0e\x06\x1a~O-D CU\t\x0e\x06 E2\n\x17bA#\x0b\t>O\x11\x011O\tH*\x1b\x10-\x08\x00)E\x02\nMck~)\x07"\x01H*+\n_\x01\x00\x00\x00c\n\x00!\x12V\r\x1d4A\x19\x16\x0b"O!N(\x00\x13Dy\x02\x000\x08\rn\x16\x19E\x16,\x0fS\x17H+\x1c\x03N)\nEU1\x0e\x01c\x10\x1b+\x16\x02\x0c\x1d-A\x11\x15\r8\x16H\x0f#\x0e\x0cOx'
and the secret key - YouCanNeverCatchJohnDoe!
We also intercepted the name of his account - 31zdugxvkayexc4hzqhixxcfxb4y
Author: NoobMasterGiven is a XOR key YouCanNeverCatchJohnDoe! alongwith some random encrypted text. I decrypt it using the following python code:
encrypted=""
xor_key = 'YouCanNeverCatchJohnDoe!'.encode('utf-8')
decrypted = bytearray()
key_length = len(xor_key)
for i in range(len(encrypted)):
decrypted_byte = encrypted[i] ^ xor_key[i % key_length]
decrypted.append(decrypted_byte)
decrypted_message_str = decrypted.decode('utf-8')
print("Decrypted message:", decrypted_message_str)By decrypting, I get this:
John Doe's Assistant: Hey, John Doe! What you listening to?
John Doe: You know how much I love music so don't ask me that question every again!Now I am also given a username:
31zdugxvkayexc4hzqhixxcfxb4yNow in the decrypted text, I found that it talks about how much John Doe loves some music, so I tried to find some account for this username on NameCheckup.

Here the grey ones mean that username is taken and the only grey one for music is Spotify so I clicked to check and got this:
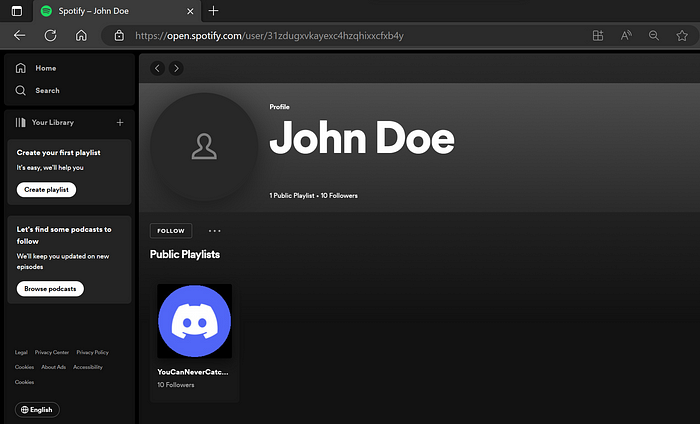
On checking the playlist, it had another hint.

The profile picture is of Discord so I checked the CTF server to see for any John Doe thats where I found him.

So now I went to the CTF website and found him here:


Now we got more encrypted text:
\r\x07\x1c-\nN\x19\x04\x0fE0"\x02\x1f7\x00#\x01\x03N\x13\x0e\x1c\x01
By decrypting it using above given script I got this:
Think Way BackThink WayNow this instantly meant using Wayback Machine. Now I entered the URL of the page where I found him team on page 8 on Wayback Machine.


I got one hit on 2023. I opened it up.

Now there is a redirect option in the Website of John Doe’s team. So I went on it to find a secret page.

https://ctf.n00bzunit3d.xyz/t0ps3cr3tBy visiting the page it had nothing inside it. All empty. I inspected it using Inspect Element and found more encrypted text.

Basically it was written in same font as background lol.

Now I decrypted this text using same script and got the flag.
n00bz{n0_0n3_c4n_3sc4p3_MR.051N7,_n0t_3v3n_J0HN_D03!}Hope you liked it. Do give it a clap and follow me for more if you enjoyed it.










